信呼
为企业构建一个基于互联网的企业管理平台, 对企业中沟通与互动,协作与管理的全方位整合,并且免费开源系统,二次开发更快捷,即时推送审批,掌上APP手机办公。
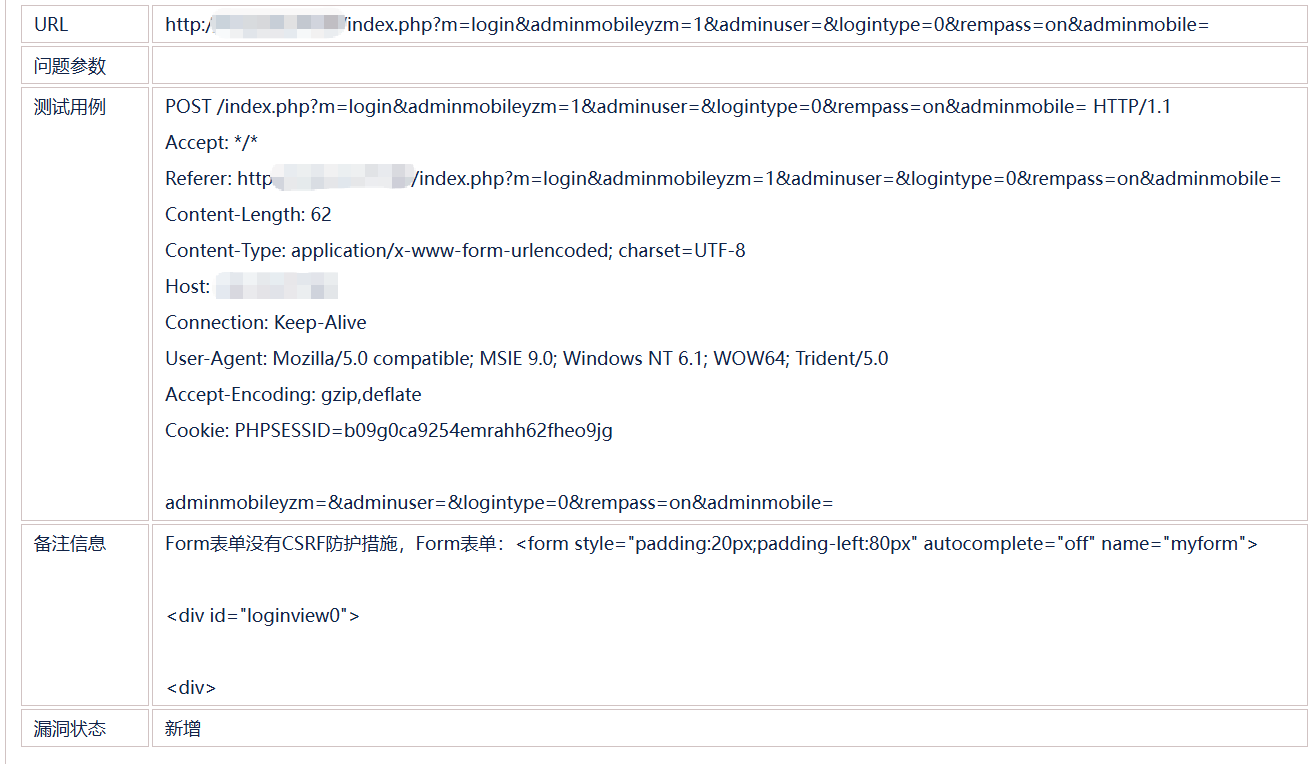
Form表单无CSRF保护的漏洞
浏览次数(24495+411),最后更新(2025-09-25 16:41:11)
系统被奇安信网神进行漏洞扫描时,出现了 Form表单无CSRF保护的漏洞
测试用例:
POST /index.php?m=login&adminmobileyzm=1&adminuser=&logintype=0&rempass=on&adminmobile= HTTP/1.1
Accept: *
Referer: http://xxxxxxxx/index.php?m=login&adminmobileyzm=1&adminuser=&logintype=0&rempass=on&adminmobile=
Content-Length: 62
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Host: xxxxxx
Connection: Keep-Alive
User-Agent: Mozilla/5.0 compatible; MSIE 9.0; Windows NT 6.1; WOW64; Trident/5.0
Accept-Encoding: gzip,deflate
Cookie: PHPSESSID=b09g0ca9254emrahh62fheo9jg
adminmobileyzm=&adminuser=&logintype=0&rempass=on&adminmobile=
原创文章,禁止转载复制,信呼OA官网保留一切知识产权。
-
 1楼 官网、 (2025-09-25 19:14:05) 看不懂
1楼 官网、 (2025-09-25 19:14:05) 看不懂 -
 2楼 SVIP、 (2025-09-26 10:48:54) 网信部门使用漏洞扫描工具扫描时发现,系统的form没有csrf防护措施
2楼 SVIP、 (2025-09-26 10:48:54) 网信部门使用漏洞扫描工具扫描时发现,系统的form没有csrf防护措施
评论回复(2)


